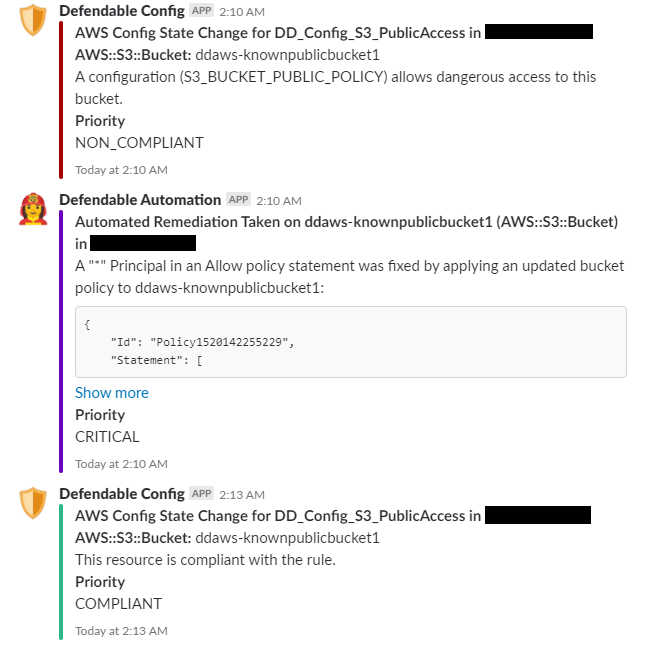
An alarmingly large number of severe data breaches lately have been attributed to poorly configured S3 buckets. Unfortunately, we see this time and time and time again.
The good news is that latest update to DD-AWS now includes self healing for leaky S3 buckets 🎉.
How it works
-
A custom AWS Config Rule checks S3 buckets for dangerous permissions in real time (almost) whenever a change occurs.
-
When a bucket is detected as non-compliant, the Config Rule status changes, and a remediation task is pushed to an SQS queue.
-
The
Remediation_CoordinatorLambda function periodically (every 1m) pulls tasks from the Remediation queue and fires off the correct function to fix the problem, in this case theS3_PublicAccess_Remediationfunction. -
The
S3_PublicAccess_Remediationfunction will selectively remove the dangerous part of the Access Control Policy, or Bucket Policy and then call the AWS API toPutBucketAclorPutBucketPolicyto remediate the risk. -
If you’ve enabled Slack integration, the
Notifierfunction lets you know everything that’s happening, at every step of the way:
What it looks like in action
What it costs
DD-AWS is open source and is released at no cost under a MIT license.
The current version costs around USD $10 per month to run from underlying AWS infrastructure costs. This price will depend on the volume of your CloudTrail logs for S3 and CloudWatch Logs storage costs.
Get it from GitHub
Download the latest release from GitHub to try it out: https://github.com/DefendableDesign/DD-AWS/releases/

Comments