If you’re not already aware of the Center for Internet Security, they’re a non-profit organisation who do amazing work to help infosec practitioners and sysadmins harden their systems.
CIS produce a series of Benchmarks (among other things) for a wide variety of technology tools and platforms. The CIS Benchmarks provide best-practice guidance on how to secure these systems.
Helpfully, the CIS AWS Foundations Benchmark tells you what you should do to help secure your AWS account.
Measuring better
You can quickly test how your own AWS account ranks against the benchmark using the aws-cis-foundation-benchmark-checklist from AWS Labs.
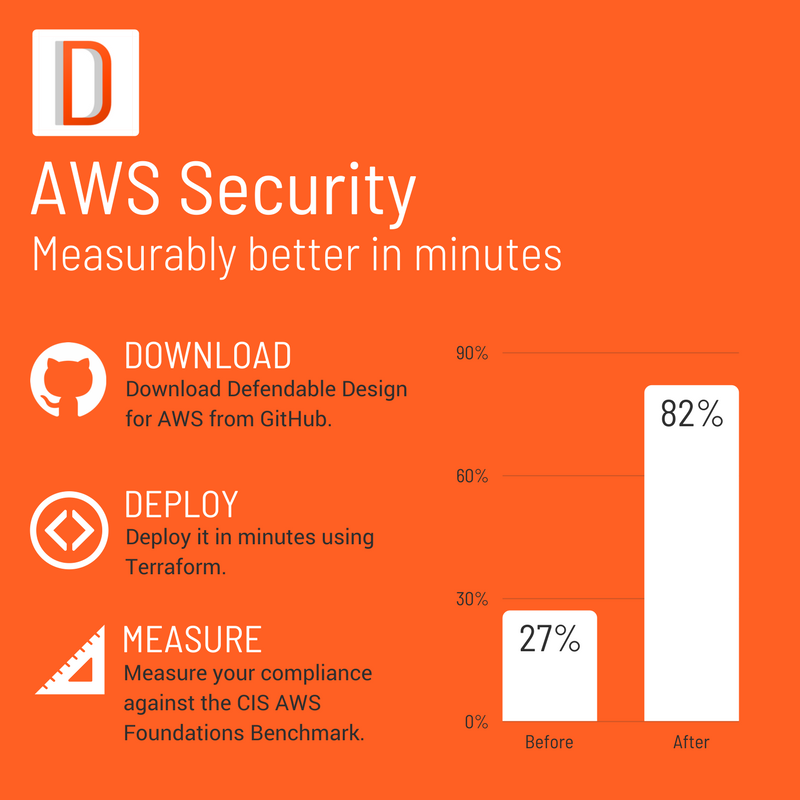
Given that the latest updates to DD-AWS include better coverage against the benchmark, I thought I’d do a quick before and after comparison.
For the sake of keeping it simple, I’ve excluded any of the manual checks from my scoring, and only count the controls that the benchmark defines as scored.
| Before DD-AWS | After DD-AWS |
|---|---|
| 27% 😞📉 | 82% 😊📈 |
Obviously, your mileage may vary, and depending on how you run things the numbers in your own account might differ.
Download, deploy, measure
Download the latest release from GitHub to try it out:
https://github.com/DefendableDesign/DD-AWS/releases/
Deploy it using the instructions here:
https://github.com/DefendableDesign/DD-AWS/blob/master/README.md
Be mindful that if your account is in a bit of a sorry state, it might be better to leave enable_auto_response off (it’s off by default) until you’re sure that you’re not relying on any bad security groups or public S3 buckets.
When it comes to cost control 👛, DD-AWS costs me around $10 (USD) per month to run. Depending on your existing free tier consumption, and the volume of CloudTrail and Config events, you might pay more than this.
Measure your compliance with the benchmark, before and after using AWS’ checklist tool: https://github.com/awslabs/aws-security-benchmark/tree/master/aws_cis_foundation_framework

Comments